The school of algorithmic solidarity
‘The school of algorithmic solidarity’ proposes to clash together two contradictory vectors: algorithms and solidarities, attempting for not-solvable, provocative, going-to-mad, having-no-answer, inventory, imaginative. Specifically looking into infrastructural time, algorithmic abstractions and bodies. By form, it can be a collective experience / radical pedagogy practice / walk to the specific location / LARP protocol / digital togetherness / open-ended situation / affective temporary training zone. Each time one of the ??????????????ions is raised that forms the logic and poetics of a session. The school operates spontaneously, without a permanent space or temporality, being unstable and fragile, occupying city holes for its actions, online spots for hacking their seemingly spotless interfaces, friendly initiatives’ spaces, exhibitions and gardens. It is an attempt to gather a quickly-assembled community, temporary forum, fictional connections (that by their affect can potentially become non-fictional), algorithmic forms of communality and commoning.
The series of collective experiments and situated experiences that seek to answer the questions:
can colonialism be encoded into algorithms?

Supporting materials:
What was there?



- set up of speculative environment of the code
- collective reading
The session looks into the recent leaked source code of biggest IT corporation which is very close to russian government. The source codes of the “Yandex” company were copied in July 2022 and published in the Internet on January 25, 2023. The size of the leakage is 44,71 gigabytes. A proposition is to read the code collectively, diving into:
encoded ownership on territories
exceptional cases
patterns of digital colonialism
how-to-spell constructedness
“pure web”
encoded violence
fairy tales about oil
Conditions: { Tag: "war" Check { # update according to the situation Expression: "0" } }/* If Russia (country) from Russia's point of view (001) contains Crimea and from Ukraine's point of view (UA) doesn't contain Crimea, we build 2 variants of Russia. It means, that countryToRecognitionSubjects contains Russia [001, UA]. */
No necessary programming or any other skills are needed.
The leaked code is the code of different services, developed by yandex company:
- yandex disk, analogue of google drive
- artificial intelligence assistant, yandex alisa
- maps
- internal services
- business to business applications, advertising, metrics (Metrika, which collects user analytics through a widely used SDK, and Crypta, yandex’s behavioral analytics technology)
- taxi
- delivery.
We started to make a counter search engine to navigate through and be able to share it. It is running on our server which we turn on and off, because of the huge amount of data.
As the source code was dumped in July 2022, there is some evidence of the ongoing russian war of agression against Ukraine at that time. With traces of annexation of Crimea, with relations/traces of the strategies of the company of expanding on the territories of Belarus, Kazakhstan, Armenia, Georgia, Serbia, Turkey, and others.
At the space, or during the running time of our server, you can access a search engine, where you can type a word or a phrase, and then you would see files where your searched word/phrase appears. The code is in English, a lot of data is in Russian, Turkish, and other languages. Try to type a word or phrase of your interest. Look at the directory from where the found file is coming, try to analyse it. No programming or any other skills are needed to search. Please feel free to contact us for any assistance, help, or questions: eeefff.org@gmail.com.
Several readings took place in Ngbk as part of Өмә exhbition, HU Media Lab as part of cooperation between berlinergazette.de, Critical Data Lab and eeefff, coming up in ACUD.
when the politics of the street intersects with the politics of digital materiality?

What was there?
A collective walk to the places connected to: mobile operator that blocked the network during the revolutionary events, parking area without network coverage, waterworks and passing-by surfaces.

how to steal the diamond of knowledge?
Supporting materials:

What was there?

A training session on occupying the public media infrastructures — media surfaces that do not belong to us. When you come to this training session, it appears that the session has already happened and you took part in it before. Look inside of some of the RECORDINGS that you made to find out what was there:
lying-on-grass-ndg.mov

backup-03.mov

screen-images-06.mov
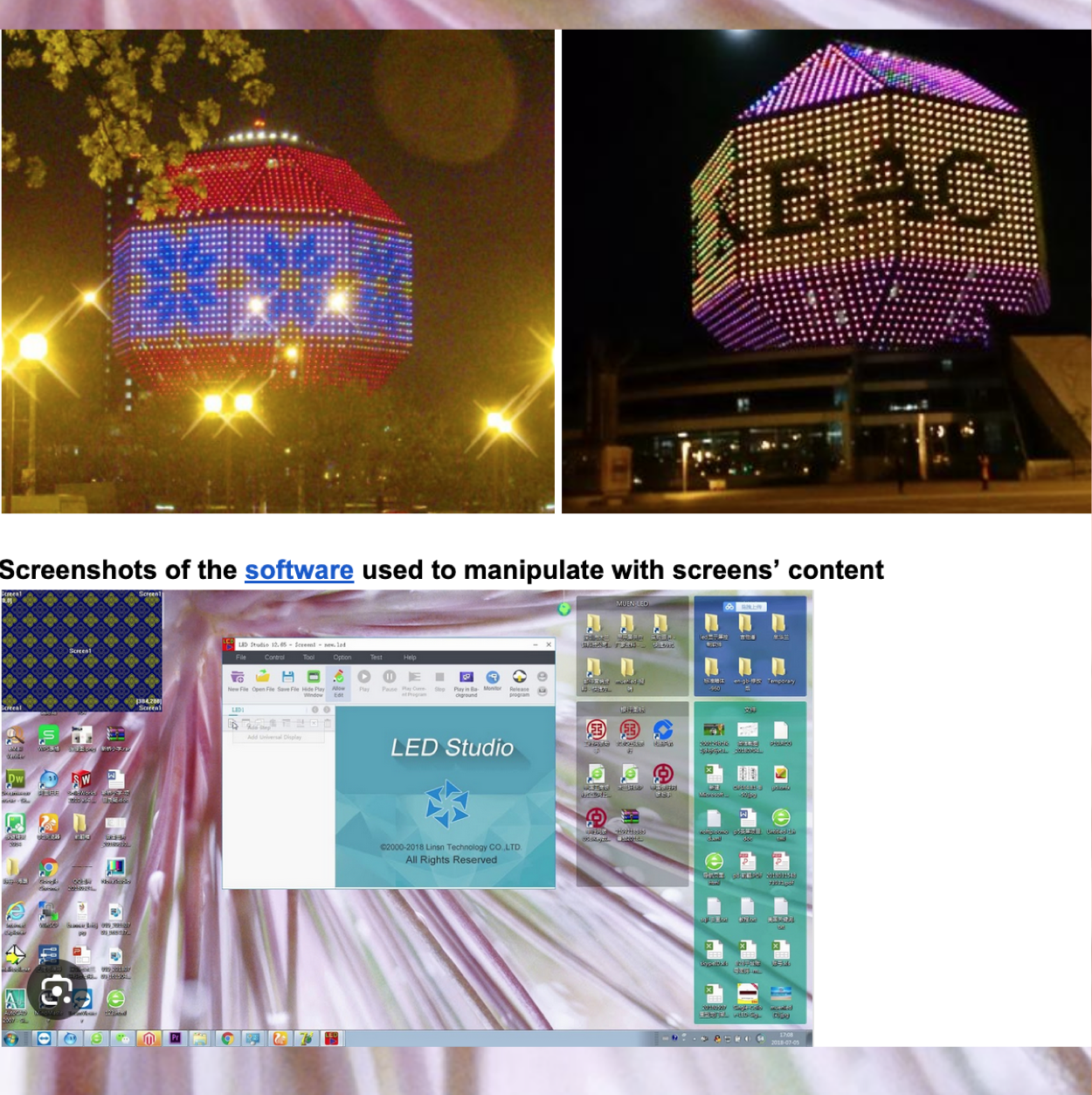
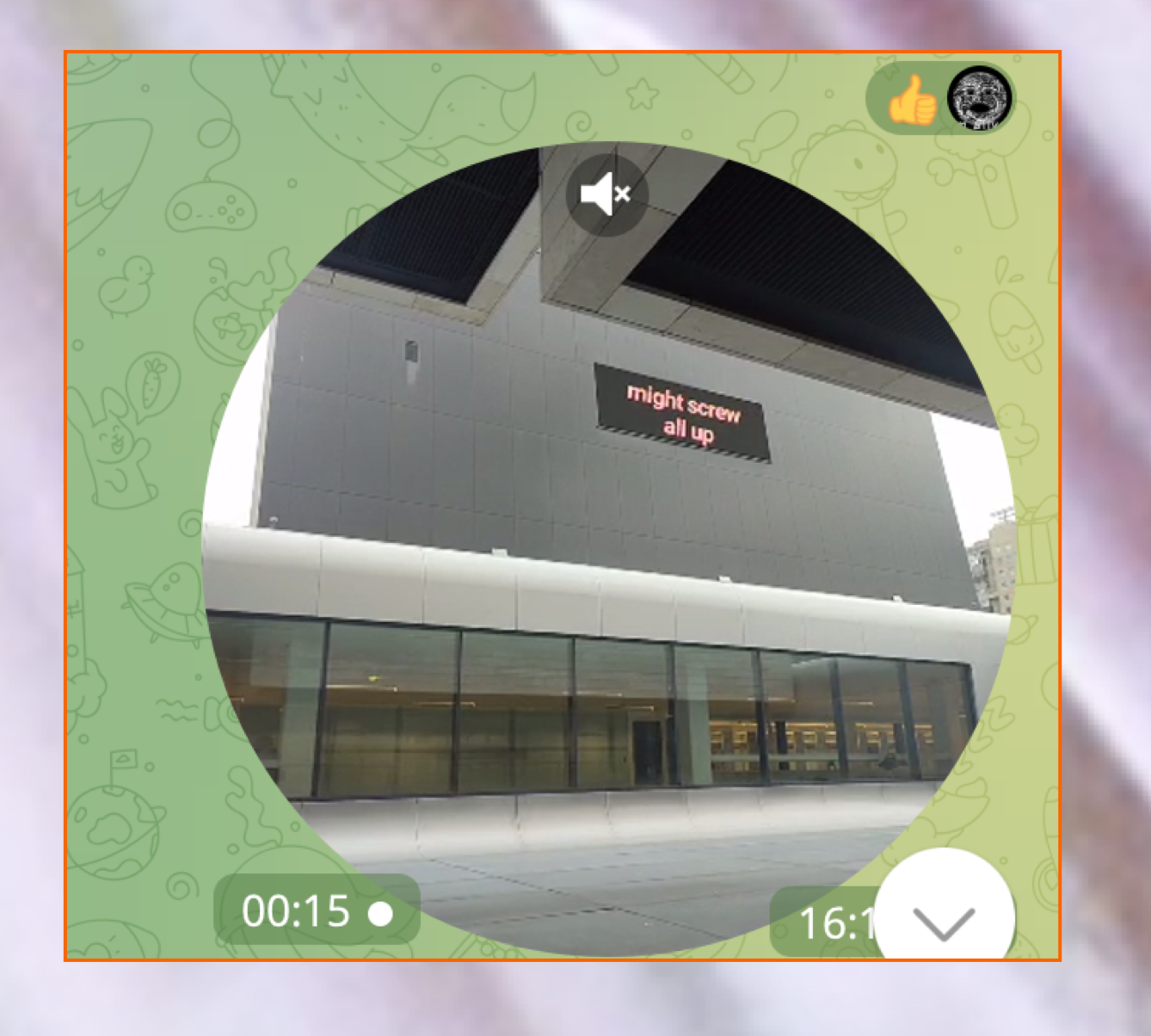
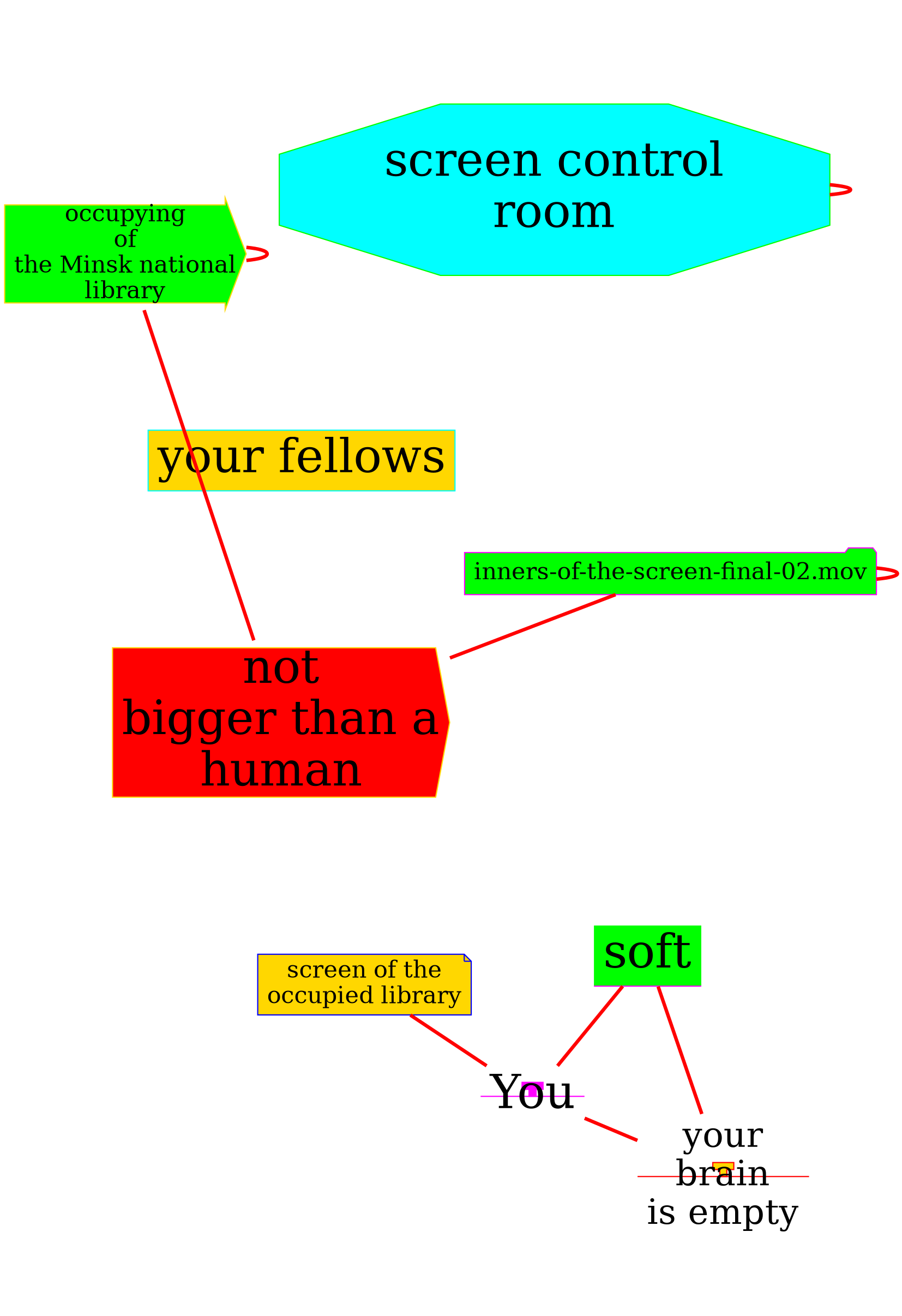
You draw a shape of the National Library in Minsk, someone called its building “Diamond of Knowledge” (See Appendix), each of you spend time on your own to think about what could appear on the screen of the occupied library.
Some of you decided to concentrate on algorithmic “dictatorships”, on hidden power structures that are “behind the screen”. Some – to use the screens as the point of information. Some decided to send a message for the military festival participants that is happening nearby. Some just wanted to say hi to their family members… Some… Some…
run-02.mov
Your group trains to run in different directions. So that you know exactly where you will run to if something goes wrong. One of you plays a security guard. Others are running away. Every next round, the person playing security guard changes.

inners-of-the-screen-final-02.mov
You have a call with the person who has access to the screen control room. You are shown the software used to manipulate with screens’ content

skills-to-be-trained-02.mp4
You decide that a ground of NDG is a perfect location to train the hacking and occupying of the Minsk national library.
upstairs-03.mp4
You go inside of the screens. Go up the stairs. You see a box on the opposite side of that box there is the screen. You open it. And see some electronics produced by the company named “screen.by” (See Appendix). Here one of you is telling, how you first started to think about the infrastructural connection between NDG and one of the Belarusian company – which also makes screens for the presidential administration –, when your friend showed you this finding.
is it possible to feel the infrastructural time?
Supporting materials:
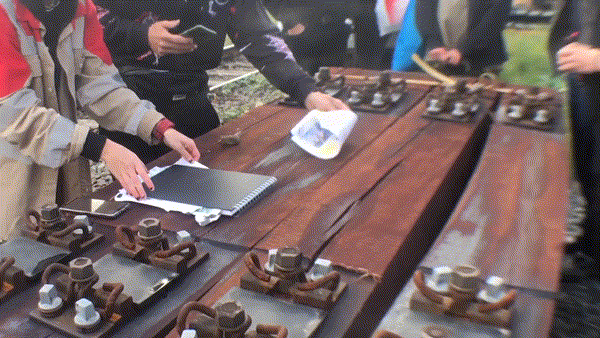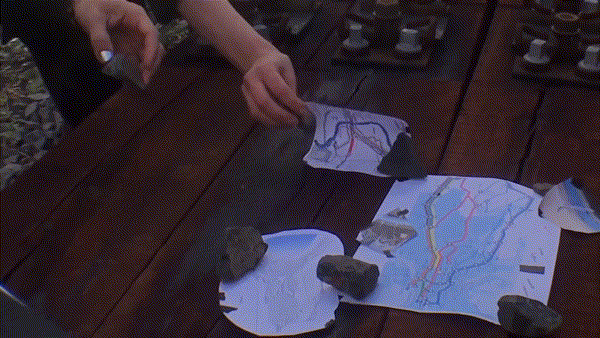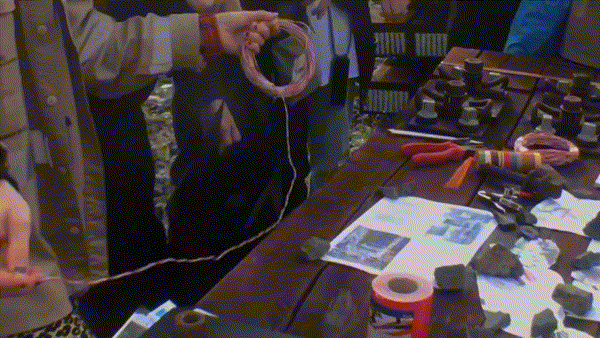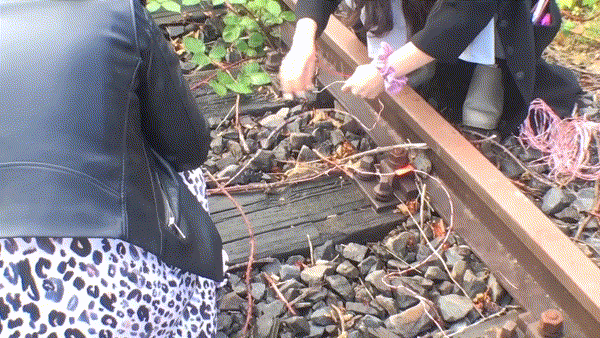
- pliers
- clamps
- copper wire
- gloves
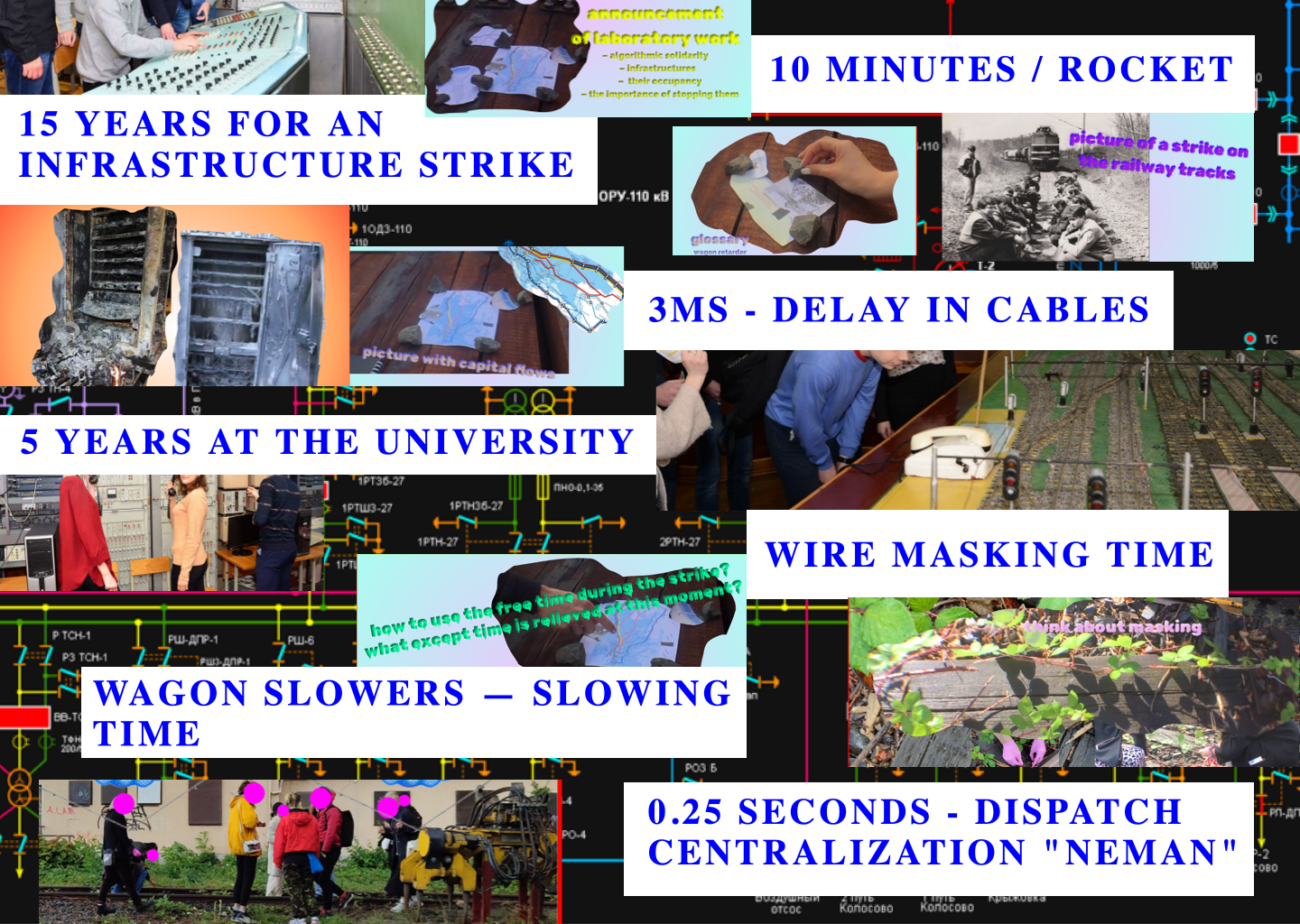
What was there?
- we went to the specific location, with abandoned railway tracks
- we created our own “train slowers/retarders”
- there was also an experiment with installing the calendar on your phone ADD THE CALENDAR TO YOU

In this session, we wanted to work with infrastructural time and how it can be embodied (if even it is possible). Taking some concrete timing events – delays in cables, time to get particular knowledges about a railway infrastructure, time of burning the cabinets responsible for the algoritmization of the railway in case of sabotage, time of flying rocket from Gomel region to Kyiv, time of masking the wires that can make a signal for the whole system to slow down the train, time of a decision of an operator in a control room – we were shuffling around them, trying to navigate and be navigated, trying to mix the “precision of the computer” with events that act upon it, that can be error-friendly towards the infrastructures, that can wrestle this precise time down. As we think we need to unpack the seemingly untouchable algorithmic processes — they could be actually interrupted, mutable, shakable.
This session took place in Kassel as part of friendly Antiwarcoalition invitation, 2022.

HERE you will can excess the infrastructural time story that we tried to gather.
can we redefine what is called as “artificial intelligence” in socio-political terms?
Supporting materials:
- web-page with exercises, reading ideas, and links to existing artistic works, scientific research, tools from concrete nowadays neoliberal corporations
What was there?
There were 5 main working zones that we exercised with:
COMPAROLOGY
Exercises that look into metrics that are used in different text-to-image models and image generators.
DATASETS
Exercises with “AI” datasets that are used to make: a) hierarchy of words and concepts, b) recognition of movements, c) recognition of emotions.
EXTRACTIVISM
Exercise that looks into where the data is stored physically in an urban space, what are the costs of computations.
INTIMATE INTERFACES
Exercise to navigate through material level of AI technologies. We have looked into consumer products like the Amazon Echo to consider the underlying data collection and resource extraction.
LABOUR INTERFACES
Exercise with interfaces. We have tried out two interfaces: a) Interface of manager, b) Interface of labour of micro-tasker, or ghostworker. We have learnt-by-doing, what “labeling” of data is, what processes stays behind “AI” models, who is doing what to maintain these models afloat.
Here you can excess the script for these 5 zones:
too close to reality? at what point do virtual maps become real?
This session happened using 2 “spaces” or, in order not to transfer physical understanding of the space into the digital and not to clone its logic, let’s call it 2 modes-of-being-in:
- experience of being in virtual copy of Minsk Zair Azgur Museum, which was made in frame of “Open Objects” project of Clemens von Wedemeyer.
- gameplays that were happening in a virtual map of Minsk in the “World of Tanks” video game.
Several sessions happened during the Kyiv Biennial 2023 in Vienna as collaboration between eeefff and Clemens von Wedemeyer.
Session happend during as collaboration between us and Clemens.
Watch documentation here:
Audio collage: eeefff
Virtual space of Zair Azgur Museum in Minsk: Clemens von Wedemeyer.
Screenrecording: Clemens von Wedemeyer